Featured Posts
View AllIMAFS The Inventory Optimization Software
- ikram
- April 18, 2024
- 0
Cold chain: A cutting-edge SCM and logistics perspective
- ikram
- January 1, 2024
- 0
Letter of Credit and blockchain technology in a Supply Chain
- ikram
- December 12, 2023
- 0
Post Covid-19 Supply Chains: A Brief Discussion
- ikram
- December 1, 2023
- 0
A discussion about International export and outbound logistics of goods
- ikram
- November 13, 2023
- 0
Trending Posts
View AllIMAFS The Inventory Optimization Software
- ikram
- April 18, 2024
- 0
Abstract IMAFS the inventory optimization software helps knowledge gathering areas, such as, solution oriented and…
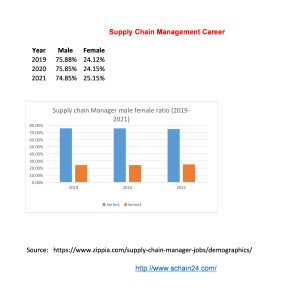
What is a Supply Chain Management Job and Career?
- ikram
- April 1, 2024
- 0
Abstract In a case study, based on US-based companies, first-level management is of about 0-4…
What is drop shipping: a supply chain distribution network option |
- ikram
- March 18, 2024
- 0
In drop-sip model, product is shipped directly from manufacturer end bypassing a retailer. Benefits of…
How to be a supply chain manager and what are the roles?
- ikram
- March 3, 2024
- 6
Abstract Supply chain managers are crucial in connecting different parts of a business’s supply chain,…
Latest Posts
View AllIMAFS The Inventory Optimization Software
- ikram
- April 18, 2024
- 0
Abstract IMAFS the inventory optimization software helps knowledge gathering areas, such as, solution oriented and stock availability management, best practices in inventory management, support from experts, evolution of ROI before…
What SCM Professionals Overlook When it Comes to Optimizing!
- ikram
- October 25, 2023
- 0
Decreasing the amount of packaging a firm is using can reduce waste and increase positive public perception of your organization. Ideally, a supply chain will be conscious of the cost-cutting…
How Does Semiconductor Technology Impact the Global Supply Chain?
- ikram
- October 13, 2023
- 0
The industry`s annual semiconductor sales revenue has since grown to over $481 billion, as of 2018. In 2021, the sales of semiconductors reached a record $555.9 billion, up 26.2 percent…
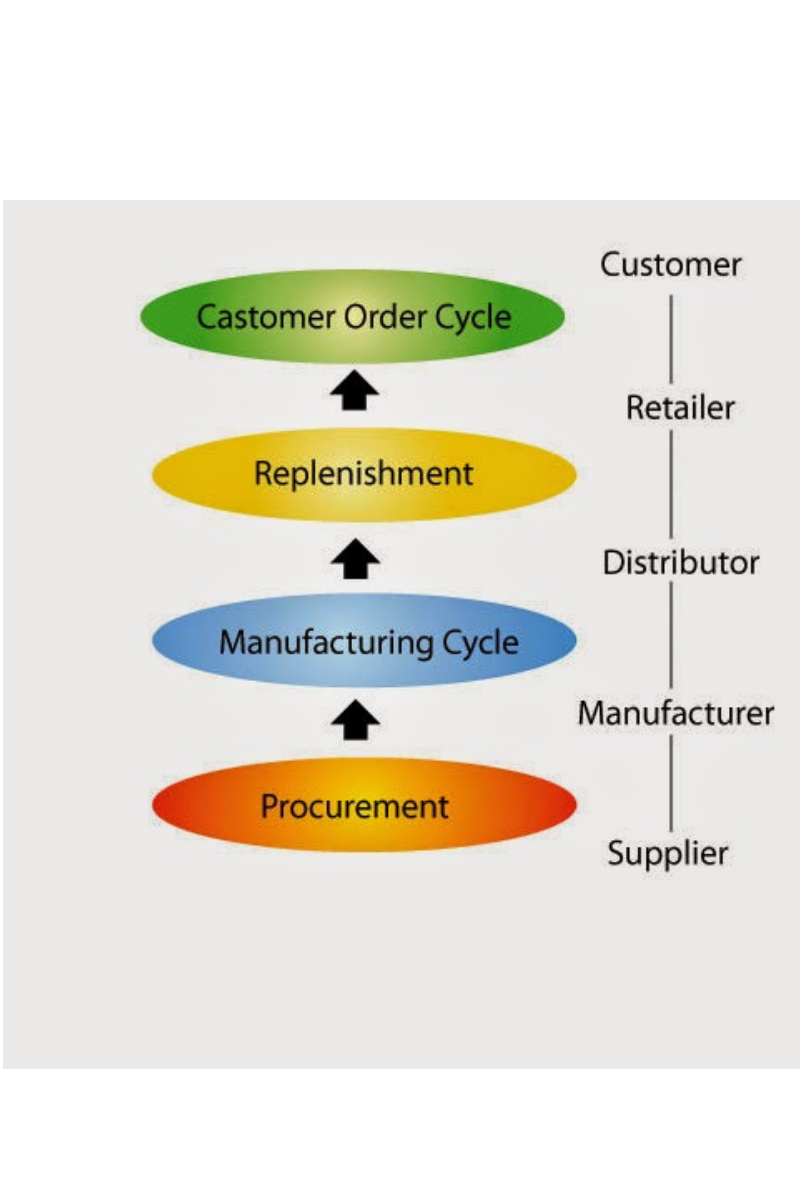
Cycle View of a Supply Chain: The Processes ।
- ikram
- October 1, 2023
- 8
The processes in a Supply Chain are usually divided into a series of cycles, each performed in the interface between two interrelated successive stages of a Supply Chain. Sub-processes in…
How supply chain planning works: A general discussion
- ikram
- September 18, 2023
- 0
The uncertain nature of the customer demand need to take into consideration by generating the production plan and in particular the production quantities, to meet uncertain customer demand in the…
Supply Chain Management
View AllIMAFS The Inventory Optimization Software
- ikram
- April 18, 2024
- 0
Abstract IMAFS the inventory optimization software helps knowledge gathering areas, such as, solution oriented and stock availability management, best practices…
A discussion about International export and outbound logistics of goods
- ikram
- November 13, 2023
- 0
In the export trade, goods and services are sold and shipped out of the jurisdiction of the country and customs…
How supply chain planning works: A general discussion
- ikram
- September 18, 2023
- 0
Vaccine Supply Chain Management in covid-19 perspective
- ikram
- September 13, 2023
- 0
IMAFS The Inventory Optimization Software
- ikram
- April 18, 2024
- 0
Abstract IMAFS the inventory optimization software helps knowledge gathering areas, such as, solution oriented and stock availability management, best practices in inventory management, support from experts, evolution of ROI before…
What is a Supply Chain Management Job and Career?
- ikram
- April 1, 2024
- 0
Abstract In a case study, based on US-based companies, first-level management is of about 0-4 years. To understand the supply chain management job and career we can remind ourselves about…
What is drop shipping: a supply chain distribution network option |
- ikram
- March 18, 2024
- 0
Abstract In drop-sip model, product is shipped directly from manufacturer end bypassing a retailer. Benefits of aggregation can be achieved, if the manufacturer can keep some of its inventory at…
How to be a supply chain manager and what are the roles?
- ikram
- March 3, 2024
- 6
Abstract Supply chain managers are crucial in connecting different parts of a business's supply chain, ensuring the value of the supply chain increases through effective management of supplier support, transportation,…
IMAFS The Inventory Optimization Software
- ikram
- April 18, 2024
- 0
Abstract IMAFS the inventory optimization software helps knowledge gathering areas, such as, solution oriented and stock availability management, best practices in inventory management, support from experts, evolution of ROI before…
Cycle View of a Supply Chain: The Processes ।
- ikram
- October 1, 2023
- 8
The processes in a Supply Chain are usually divided into a series of cycles, each performed in the interface between two interrelated successive stages of a Supply Chain. Sub-processes in…
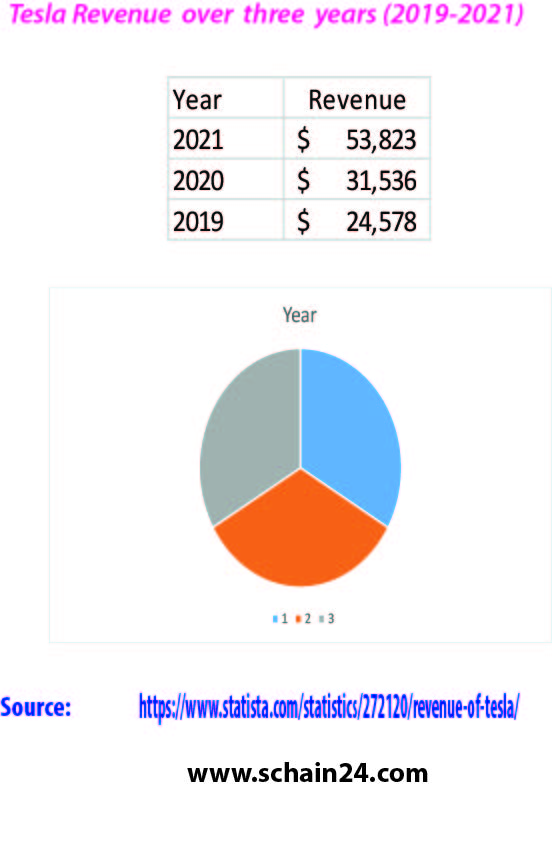
Tesla’s supply chain and logistics: A case study
- ikram
- May 1, 2023
- 0
The company was incorporated as Tesla Motors, Inc. on July 1, 2003, by Martin Eberhard and Marc Tarpenning. Eberhard verbalized he wanted to build a car manufacturer that is additionally…
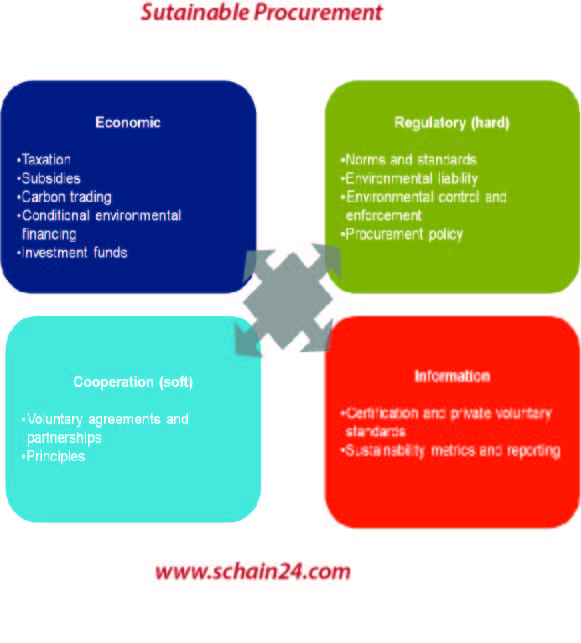
Sustainable Procurement: A Concept Used In SCM And Beyond.
- ikram
- August 2, 2023
- 0
There are different levels of focus in the dimensions of sustainability and also sustainable procurement. Focus on the supply chain network entails managing and balancing the supplier portfolio. The impact…
H & M Supply Chain management: A case study
- ikram
- January 8, 2023
- 0
Hennes & Mauritz AB is a Swedish multinational clothing-retail company known for its fast-fashion clothing for men, women, teenagers, and children. As of November 2019, H&M operates in 74 countries…
Trending
View AllIMAFS The Inventory Optimization Software
- ikram
- April 18, 2024
- 0
What is a Supply Chain Management Job and Career?
- ikram
- April 1, 2024
- 0
What is drop shipping: a supply chain distribution network option |
- ikram
- March 18, 2024
- 0
How to be a supply chain manager and what are the roles?
- ikram
- March 3, 2024
- 6
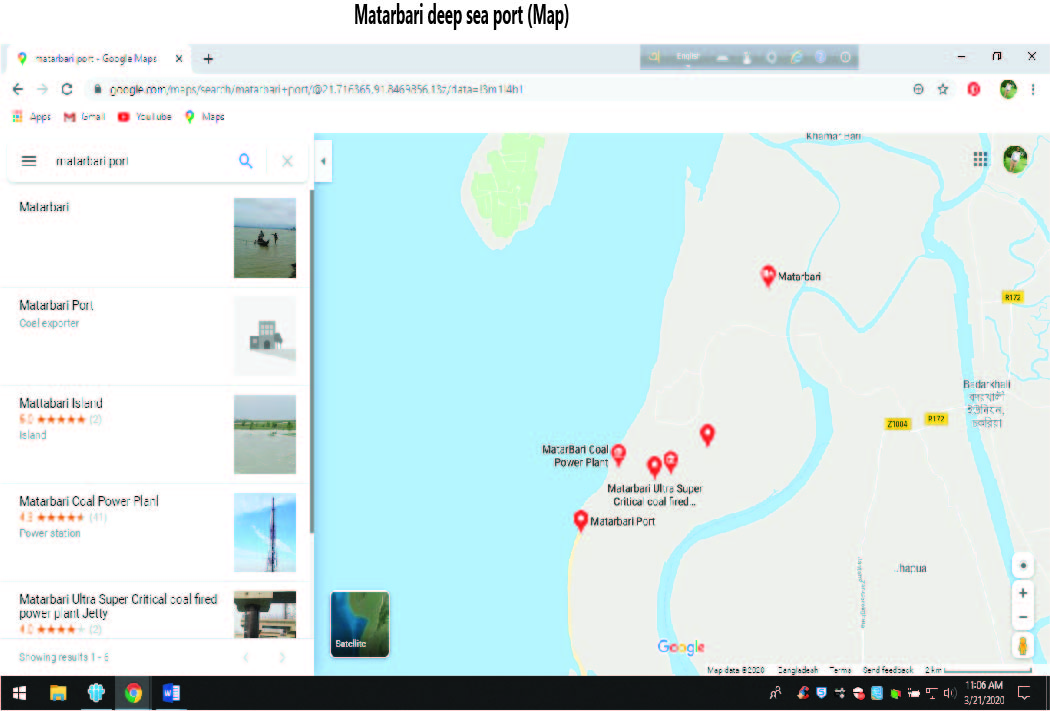
About the Matarbari deep sea port: An SCM perspective
- ikram
- February 4, 2024
- 0
Editor’s Picks
View All
Follow Us On
Popular Posts
View AllRecent
View AllIMAFS The Inventory Optimization Software
- ikram
- April 18, 2024
- 0
Abstract IMAFS the inventory optimization software helps knowledge gathering areas, such as, solution oriented and…
What is a Supply Chain Management Job and Career?
- ikram
- April 1, 2024
- 0
Abstract In a case study, based on US-based companies, first-level management is of about 0-4…
What is drop shipping: a supply chain distribution network option |
- ikram
- March 18, 2024
- 0
In drop-sip model, product is shipped directly from manufacturer end bypassing a retailer. Benefits of…
How to be a supply chain manager and what are the roles?
- ikram
- March 3, 2024
- 6
Abstract Supply chain managers are crucial in connecting different parts of a business’s supply chain,…