Abstract:
Standard supply chain security arrangements include: creating credentials of participants in the supply chain, finding, validating contents of cargo being shipped, notification of the contents in advance to the destination country, ensuring the security of cargo in transit using lock and other professional means, creating opportunity to inspect the cargo at an entry to the destination country etc. C-TPAT is a program to prevent terrorists from using supply chain resources to bring mass destruction weapons into the The United States of America. Joining C-TPAT, a business promises to take some responsibility for security through entire supply chain. Owners of the supply chain must conduct comprehensive security assessment based on C-TPAT requirements. Sudden fire eruption in a factory or other area of a supply chain also can be a threat to supply chain security. Necessary precaution must be taken against fire eruption to ensure supply chain security and loss of life as well.
Keywords: Supply Chain Management, supply chain security, Business management, C-TPAT, Supply chain management software(SCMS) etc.
Article:
Introduction:
The term supply chain security is used to enhance security of the transport and supply chain as a whole. According to UNECE, in replication to this growing challenge, the World Customs Organization (WCO) adopted the SAFE Framework of Standards in 2005 to provide a more vigorous fixate on those principles of the Revised Kyoto Convention that ameliorate cooperation among Customs administrations, provide supply chain security and facilitation at an ecumenical level to promote certainty and predictability. While Customs have always been in charge of controlling international trade in terms of enjoinments and restrictions, the aspect of securing the international trade supply chain has put growing and supplemental burdens on Customs to manage this balance. In the greater perspective, it combines traditional supply chain management requirements & global threats such as terrorism, theft, piracy etc. The C-TPAT started after 9/11 terror attack in USA to prevent similar attacks in USA.
The Security arrangement:
Standard supply chain security arrangements include: (a)creating credentials of participants in the supply chain, (b)Finding, validating contents of cargo being shipped,(c)Notification of the contents in advance to the destination country, (d)Ensuring the security of cargo in transit using lock and other professional means, (e)creating opportunity to inspect the cargo at an entry to the destination country. C-TPAT (Customs Trade Pact Against Terrorism) is about some principles agreed upon between US government, supplier and buyer. About 11000 businesses in the current world use the C-TPAT treaty. While we implement, it enhances our capability to get new order in business. Need of customs checking becomes less than usual, creates mutual understanding between buyer and seller.
Supplier’s duties:
Supplier’s duties include using ID card for employees, informing the management for any illegal act occurs, packages need to be guarded. Fire arms, and other unusual things should be checked and prohibited. Sensitives areas include Loading and shipment areas, warehouse areas, CCTV rooms etc.
C-TPAT & CBP’s role in enhancing supply chain security:
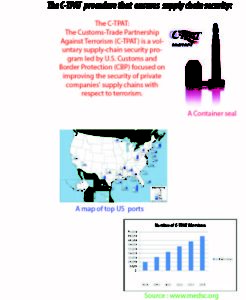
C-TPAT (Customs Trade Partnership against Terrorism ) is a program to prevent terrorists from using supply chain resources to bring mass destruction weapons into the The United States of America. The concept behind C-TPAT is simple. Joining C-TPAT, a business promises to take some responsibility for security through entire supply chain. And U.S. Customs & Border Protection (CBP) promises faster/easier processing for C-TPAT members at border/checkpoints. CBP is the unified agency within the Department of Homeland Security, responsible for the management, controlling, and protection of US borders at and between official ports of entry. Owners of the supply chain must conduct comprehensive security assessment based on C-TPAT requirements. Canada has a program similar to C-TPAT, namely, “Partners in Protection”.
Other similar programs:
Other Supply Chain Security programs are namely, Container Security Initiative (CSI), Free and Secure Trade (FAST), the 24-Hour Rule, Automated Commercial Environment (ACE) etc.
Factory level application of C-TPAT:
A factory in an apparel supply chain usually has to make a documented declaration that they are aware of the US Customs service’s C-TPAT program to combat terrorism and agree to maintain sufficient controls to ensure. And sign the Declaration on behalf of manufacturer/shipper, which declaration is a bit different for different ship mode such as LCL or DCL sea shipment or air shipment.
C-TPAT Modules:
The C-TPAT modules involve record and documentation, individual and personal security, IT security, shipment security control, storage and distribution, export and logistics, transparency in supply chain, physical checking, fulfill business partner requirement. Departments such as security department, finished goods warehouses, human resources department, IT and material control departments are directly involved to get C-TPAT agreement materialized. Other Supply Chain Security threats include Natural calamity such as cyclone, typhoon, earthquake etc. Japan earthquake and US Cyclone in 2012 are a recent example of supply chain security threats. And sudden fire eruption in a factory or other area of a supply chain also can be a threat to supply chain security. Necessary precaution must be taken against fire eruption to ensure supply chain security and loss of life as well.
SCMS and Supply Chain security best practices:
Supply-chain-management software (SCMS) is the software tools or modules used in executing supply chain transactions, managing supplier relationships and controlling associated business processes. Supply chain management maximizes the efficiency of business activities that include planning and management of the entire supply chain. It helps businesses in product development, sourcing, production, and logistics by automating operations. In this way, it increases the physical flow of business as well as informative flow. The entire business benefits with higher performance, greater cost-efficiency, and thus increased supply chain efficiency. We should not use software if not required. Especially, freeware, browser extensions and plugins are great source of cyber related attacks. We should check first if we need it. Need to use Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) systems to detect exceptions in our orders. Patch control is also essential to avoid such attacks.





thanks for sharing this post
I know this if off topic but I’m considering starting my own, personal weblog and was
curious what all is needed to get set up? I’m assuming possessing a blog like yours would cost a pretty penny?
I’m not very web smart so I’m not 100% positive. Any suggestions or advice can be greatly appreciated.
Thanks
Thanks for your message.You can start with blogger.com , which is free.
Wow, awesome blog layout! How long have you been blogging for? you made blogging look easy. The overall look of your web site is magnificent, let alone the content!